-
Here's the pitch: a 10-inch, almost-pocketable computer running Snow Leopard, the latest, greatest version of OS X. It costs just $300. Sound good? Here's how to make your own.
Transcript & comments from "Twitter against Tyrants" Congressional hearing
Some choice adhoc quotes that tumbled out of my brain during the Congressional hearing on new media, titled “Twitter against Tyrants”, that I spoke on last Thursday in Washington, D.C..
“I’ve learned an important lesson in working with the Tibetan
independence movement and others: It’s that we can’t presume what people are
willing – are or are not willing to do for their own freedom and liberty and
democracy. We can’t say, oh, if they do that, they might get arrested or go to
jail or get killed and we can’t do that. These are people, as we saw in Iran,
who are willing to take to the streets and die for their freedom, and you know,
the – it’s an important fact to remember to not presume that you want to
protect them.”“I get asked this question a lot as well because I’m building,
like, an encrypted phone and people are like oh man, the Mafia is going to love
that, or something. So it is – and my students ask me this as well – and I
don’t, from an engineer perspective, I don’t want to be the guy that said yeah,
just, I made the AK-47 and you know, it’s a great gun. (Laughter.) So you
have to be careful. You need to inject morality into these things, but you do
– it’s a slippery slope.”“I’m happy for tools like Twitter, that they can be used just as well to cover
the daily lives of Ashton and Demi or break the news of Michael Jackson’s
death. But the fact that they can be used to broadcast updates from the
streets of Iran or spread the news of political prisoners in Tibet being
executed is a very weighty obligation and responsibility that they’ve taken on.”
Many thanks to my fellow panelists (Daniel Calingaert, Evgeny Morozov, Chris Spence and Shiyu Zhou) for the enjoyable discussion.
Shout-outs to Ushahidi, Alive in Baghdad, Lech Walesa and more in the full un-official transcript.
Orbot: An Anonymous Proxy for Android using Tor
I’d like to make this post without much fanfare. Just looking to share information on the work I’ve been doing with the fantastically radical team over at the Tor Project, as part of my work on the Guardian Project. We have successfully ported the native C Tor app to Android and built an Android application bundle that installs, runs and provides the glue needed to make it useful to end users…. secure, anonymous access to the web via Tor on Android is now a reality. (Update: Tor doesn’t magically encrypt all of your Internet activities, though. You should understand what Tor does and does not do for you.)
However, there is still much work to be done… read on!
1) Tor 0.2.2.5-alpha release contains all the necessary code for building the Tor binary exe using the Android C SDK. I utilized http://github.com/tmurakam/droid-wrapper toolchain wrapper scripts to make life easier. This will produce the output Tor exe that can run on Android w/o needing root.
Update: Thanks to Jake, you can now read the updated Orbot BUILD doc for the step by step build how to.
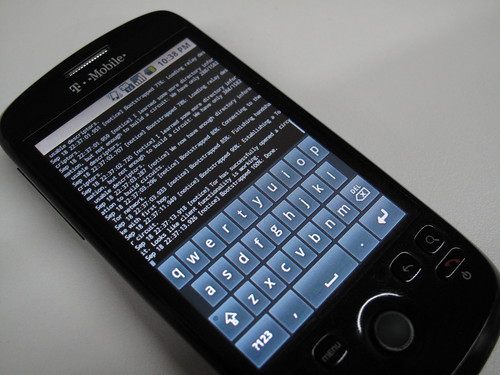
(thanks to ioerror for the pic)
At this point, we are pretty convinced that the performance and efficiency of the C binary is quite significantly better than the Java-based ports of Tor running within Dalvik… this translate to a better experience for the user, with no noticeable increase in battery drain or lag on the rest of the device while Tor is running in the background.
2) Orbot – this is the new Android app which bundles the Tor binary, handles its proper installation on the device and then provides a gui for starting/stopping, view the log and torrc, etc. It also provides a built-in HTTP Proxy and is licensed under the Tor license.
Just to be clear – we aren’t using the NDK or a shared library… we are actually extracting a binary and managing it via Runtime.getRuntime().exec() calls. This is 100% supported – who knew?! More info on how to do this here
The first code is up here… all is working, but def needs much polish:
https://svn.torproject.org/svn/projects/android/trunk/Orbot/
This post is in part a call for developers to contribute to the continued development of Orbot, so we can get it to a 1.0 state. The other big task is to modify the open-source, privacy focused Shadow browser, from the University of Cambridge DTG group, in order to make it work with our HTTP proxy. That would be a really great step forward, as right now, we have to ask users to set their global APN (read: https://svn.torproject.org/svn/projects/android/trunk/Orbot/INSTALL)
Thanks for everyone’s help and support to get here. I’d like to keep pushing on to a public release via the App Market very soon. Let me know if you’d like to contribute in any way – code, screen designs, icons, testing….
Domo arigato, Mr. Orbot-o!!
My (rough) statement for the US Helsinki Commission hearing (Feedback Please!)
Below is my rough statement for the US Helsinki Commission “Twitter v. Tyrants” hearing this Thursday. I would greatly appreciate any of your comments and feedback, as I will be polishing this up a bit before the hearing Thursday and before I formally submit it into record. I mostly wonder whether I have made to many generalizations in trying to connect the dots for people in the limited time I have. Are there other case studies I should mention that would help? Any other papers, posts, links I should I include? Thanks!
I greatly appreciate the opportunity to participate in this hearing. Thank you to the members of the commission for the invitation to appear here today, and for your interest in this very important topic. I come here today as a representative of the many, many technology advocates, experts and educators who believe that the most amazing innovations of our generation should be used for more than just acquiring more wealth or as simply new channels entertainment or distractions. I am also a longtime member and former board chair of the international non-profit group Students for a Free Tibet, led by Tibetan activists Lhadon Tethong and Tenzin Dorjee.
From my perspective, the latest wave of new media protest technology began in 2004, with an open-source web service called TXTMob. TXTMob was first developed by MIT’s Institute for Applied Autonomy for protesters at the 2004 Democratic National Convention in Boston and the Republican National Convention in New York. I was part of a team that utilized TXTMob to broadcast thousands of short messages to over 10,000 people on the streets of New York, letting them know what was happening moment by moment. Later in 2004, during the Orange Revolution in the Ukraine, students utilized the service to coordinate their spontaneous protests or flashmobs, strikes and sit-ins. In 2005, two of my colleagues who had been involved TXTMobs use during the RNC went to work for the company that became Twitter, where they showed the demonstrated the power of TXTMobs and short message broadcasting to their coworkers around the office. It was in those times, that Twitter was born. It is not an accident that things have come full circle, with Twitter now being the standard go-to tool for activists around the world.
In my activism work, my areas of focus are Asia and the Americas. I have specific experience traveling in and working with organizations focused on China, Tibet and India. I have developed patented technology, focused on the exchange of data between mobile devices over wireless networks. I am also teaching at NYU’s Interactive Telecommunications Program this semester – a new graduate course I’ve designed entitled “Social Activism using Mobile Technology”. My personal path in this sphere, as a developer, practitioner and instructor in the use of new media technologies within social movements, is built upon a very long tradition that goes back to the first time someone figured out how to use drums, fire and birds to send signal messages.
During the second world war and the cold war, inventors, mathematicians and the earliest digital computers played a critical role in helping the allies stay one step ahead of the axis. In recent years, open-source hackers, nerds and geeks have gravitated towards the social justice, environmental and human rights movements, creating unique alliances and very rich opportunity for innovation. Four guys in a garage in Silicon Valley, is now multiple activists communicating in realtime through Twitter, Skype, Facebook, all using their iPhones, Blackberries and Google Android phones, to weave together human rights campaigns using true grassroots organizing and tested non-violence tactics with open-source software, cloud-based web services and very powerful, yet very cheap hardware gadgets.
Take the case of Burma in 2007. Video journalists and I.T. student organizations teamed up to provide their own coverage of the Saffron Revolution. As their footage began reaching the outside world, they become bolder and more targeted by the junta. While the revolution never fully materialized, and many of the monks and activists who participated have been imprisoned, tortured or worse, the “VJ” model of Burma is largely considered to have been successful due to the global attention the protests received. A similar model is being used in Iraq, through the well known citizen journalist video service, “Alive in Baghdad”, that works to cover and disseminate stories of the every day lives of Iraqis. We have also seen this model used with simple camera phones in the Kashmir and most recently in Iran, where a single clip of video of an innocent dying girl instantly clarified the issue for a global audience and brought overwhelming sympathy and support to the side of the Iranian people. The power of the moving image is unavoidable.
In many cases, the authoritarian states power proves too formidable for adhoc efforts with new media technology. In Tibet, the largely peaceful uprisings in March 2008, were perceived by the outside world as being “riots”, due to China’s ability to control the story by severely restricting news media access and blocking telephone and internet communication. Thousands of Tibetans were detained, many died, and hundreds were given lengthy sentences, many convicted through evidence gathered via close-circuit security cameras, mobile phones, PCs and the Internet. There are countless stories of Chinese, Tibetan and other activists within China being incriminated through their use of email, Skype and other tools. The evidence gathered by the state is often done in collaboration with the technology providers – Yahoo!, eBay, and so on.
In August of 2008, over seventy activists from around the world traveled to Beijing to protest for Tibetan human rights and independence during the Olympic games. New media tools played a major role during this effort. It provided a loosely coupled link between the various independent activists who were traveling to Beijing to participate. It enabled a team of citizen journalists to document the many different protest that occurred (since mainstream press was mostly unable to due to their “close” relationship with Chinese security agents) – all utilizing broadcast quality HD video cameras, small mobile computers and uploading photos and footage for publishing and broadcast around the world. The Beijing authorities eventually caught on, arresting and detaining for a week, six American citizens who had been documenting the protests. During their detention, they were told that the crimes they were guilty of, documenting and spreading media of protests, was far worse a crime than actually participating in the protest itself. Fortunately, due to their American passports, they were treated fairly and made it home.
During last years presidential elections, I was a member of an adhoc team of people who came together to build “Twitter Vote Report”, a nation wide web 2.0-style election monitoring system that tied together google maps, wikis, and iPhones with human resources on the ground from watchdog groups and the media. Over 30,000 citizens reported from outside their polling places, providing a real time view and instant notice of any long lines, hanging chads and potentially voter fraud. The data captured that day was released freely to the Internet for analysis and research by academic institutions. The open-source code from this project, as well as a few others, has been utilized in India and Afghanistan, and we hope to see it become a standard tool in the fight against election fraud.
As you can tell, I am very enthusiastic and active participant in the use of new media tools for social good and in the fight against authoritarianism. However, the use of these tools also brings about the possibility of serious risk to the user, their friends, family and broader movement. As a friend of mine said, “You cannot twitter your way out of a bludgeoning by security goons”. Mobile phones are unique, always broadcasting personal identifiers; changing SIM cards does nothing, phones are tracked easily tracked by their hardware IDs. Laptop computers are often full of incriminating documents, web caches and email addresses. Digital viruses that deliver actual spy-ware such as GhostNet are common and becoming more powerful and more invisible every day – one slip and your entire email inbox can be copied by an adversary. Use of new media and social networks reveal one’s “social graphs”, buddy lists, friends & followers… in a free country, these provide benefit, amplifying your ability to communicate and connect. In an authoritarian state, these reveal your human networks, make the job of cracking down easier and more efficient. It often takes an entire generation to rebuild when an activist network is decimated. The protests of 2007 and 2008 in Burma and Tibet were at level not seen since 1988 and 1989. That twenty year gap is no accident.
While the free world is easily enamored of applications of new media tools within dictatorships and authoritarian states far way, our own federal, state and local law enforcement are often quite fearful and hostile towards their use within domestic movements. Tad Hirsch, creator of TXTMob, is the subject of a subpoena by the City of New York in connection with several active lawsuits against the City that allege police misconduct during the 2004 Republican National Convention. Elliot Madison, a 41 year old social worker, was been arrested in Pittsburgh on Sept. 24 and charged with hindering apprehension or prosecution, criminal use of a communication facility and possession of instruments of crime. The Pennsylvania State Police said he was found in a hotel room with computers and police scanners while using the social-networking site Twitter to spread information about police movements. Just this week it was announced that In-Q-Tel, the CIA’s venture capital arm, has invested in a company whose technology is capable of powerful data mining from any information openly published on Twitter, Facebook and other social networking sites. In summary, acts taken to secure our homeland from violent terrorists often have similar justifications to acts taken by authoritarian governments to squelch dissent and democracy. Our government needs to be mindful of these contradictory positions on the benefit of new media within our own democracy.
Finally, I would like to briefly emphasize the comments from Mary Joyce of DigiActive, who could not be here today, on the topic of embargoes. In the digital age, where a “good” is a string of code that can be delivered anywhere in the world with the click of a mouse, even today’s smart sanctions are not smart enough. By preventing access to blogging platforms, social networks, and other types of new media, current embargo policies harm the very activists who are furthering our common goals of democracy promotion, while leaving authoritarian governments free to spread propaganda through a range of state-controlled media outlets.
Referenced URLs of note:
TXTMob: http://en.wikipedia.org/wiki/TXTMob
Alive in Baghdad: http://aliveinbaghdad.org/
TwitterVoteReport: http://twittervotereport.com
Beijing Olympics Protest Coverage: http://freetibet2008.tv
GhostNet: http://en.wikipedia.org/wiki/GhostNet
This Thursday: Speaking at US Congressional Commission on "Twitter v. Tyrants"
I’m honored to have been asked to participate in a hearing being held by the US Helsinki Commission this Thursday, in Washington, D.C. While my enthusiasm for the power and potential of new media will be evident, I hope to bring a metered tone to this discussion, laying out a number of issues, including the risks to activists utilizing these tools, the role of corporations in surveillance, as well as issues with the U.S. Government’s own position towards the use of these tools for domestic dissent…
“Twitter against Tyrants: New Media in Authoritarian Regimes”
Thursday, October 22, 2009, 2:00 p.m.
1539 Longworth House Office BuildingThis briefing will consider the ways in which new media and Internet communication technologies affect the balance of power between human rights activists and authoritarian governments. Panelists will focus on new media’s role in protests and elections, the ways in which it empowers civil society activists, and the darker side: how dictators use new technology to control and repress their citizens.
The following panelists are scheduled to speak:
• Daniel Calingaert, Deputy Director of Programs, Freedom House
• Nathan Freitas, Adjunct Professor, New York University Interactive Telecom Program;
developer of groundbreaking technology for protests
• Evgeny Morozov, Yahoo! Fellow at Georgetown University’s E.A. Walsh School of
Foreign Service; contributing editor, Foreign Policy
• Chris Spence, Chief Technology Officer, National Democratic Institute
Read more about the briefing… Hope to see you there!


