DISCLAIMER: I am by no means an expert in this issue – I am just an an enthusiastic hacker with a dream. Also I don’t read Tibetan, but I enjoy looking at it!
Thanks to the open-source movement and the hard work of many Tibet supporters and typography experts, I am happy to announce that rendering of Tibetan characters is now supported on the most fantastic of mobile smartphones, Google Android!!!

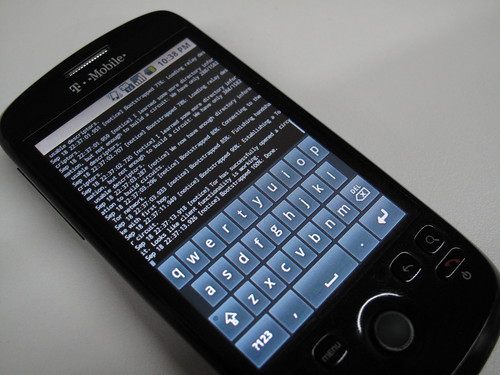
Tendor’s Yarlung Raging blog viewed on a T-Mobile myTouch3G Android Phone
While it only has a small alphabet of characters, the Tibetan language has been notoriously difficult to support on Mac, Windows and Linux due to some complexities in how one character can modify the next. Dedicated academics, volunteers and software engineers have stayed focused on solving this and the most recent versions of all major operating systems are able to render Tibetan and provide Tibetan character input tools. Google Android is based on Linux, and fortunately is able to support the use of the GPL-licensed Tibet Machine Unicode font.
However, by default Android only has a small number of fonts built-in, and doesn’t support the easy addition of new fonts or locales. It does however have something called the “fallback” font, which is used to render any encoded text it comes across that it doesn’t quite know what to do with.
What I realized is that you could replace this font with a Tibetan unicode font compatible with Linux, and that this would then enable Tibetan support in all applications on Android, including the web browser, email apps, instant messaging, and short messaging (SMS), among others.
The steps below outline the technical how to for Android users.
WARNING: This is not for novices. However, it isn’t rocket science either. Your average neighborhood mobile phone enthusiast should be able to figure out how to do this, and potentially help their friends do it too. Down the road, I hope we can make this process easier and/or Google will allow for the addition of any font to the system.
Step 1: Get Root on your Android device. You don’t need to mod your phone with a custom firmware, you just need root access to change system fonts. Here’s some places to start looking on how to (this changes weekly, btw, and differs for each type of Android phone):
Step 2: Download Tibet Machine Unicode font. You can learn more about the variety of Tibetan fonts available here.
Step 3: Make the system font folder writeable and backup the existing font
This can be done using desktop ‘adb’ tool from the SDK or the Android terminal app on the device
# su
# mount -o remount,rw -t yaffs2 /dev/block/mtdblock3 /system
# chmod 777 /system/fonts
# cd /system/fonts
# mv DroidSansFallback.ttf DroidSansFallback.ttf.bak
# exit
Step 4: Write the Tibetan unicode font as the new fallback font:
Using ADB Desktop tool with Android connected via USB
adb push TibMachUni-1.901b.ttf /system/fonts/DroidSansFallback.ttf
Using on-device terminal app:
#cd /system/fonts
#wget -o DroidSansFallback.ttf http://tinyurl.com/tibfont /system/fonts/DroidSansFallback.ttf
Step 5: Reboot your Android phone
Step 6: Point your Android browser at http://yarlungraging.blogspot.com, http://lobsangmonlam.org/ or http://tb.tibet.cn to verify the Tibetan font support is properly installed.
What’s Next
Two big steps from here… this is a call to action for Android developers out there:
- Develop a one-click app that can install Tibetan (or any other third-party language) font for any rooted device
- Port an existing Java-based Tibetan input utility into Android as an Input Method Editor so that you can have a way to write Tibetan character emails, SMS messages and blog posts.
Many thanks to the authors and developer behind the following posts upon whose work this effort was based:
karuppuswamy.com: How to change fonts in Android?
karuppuswamy.com: Mounting /system partition in read-write mode in Android
android-devs.com: Adding Additional Language Fonts to Android