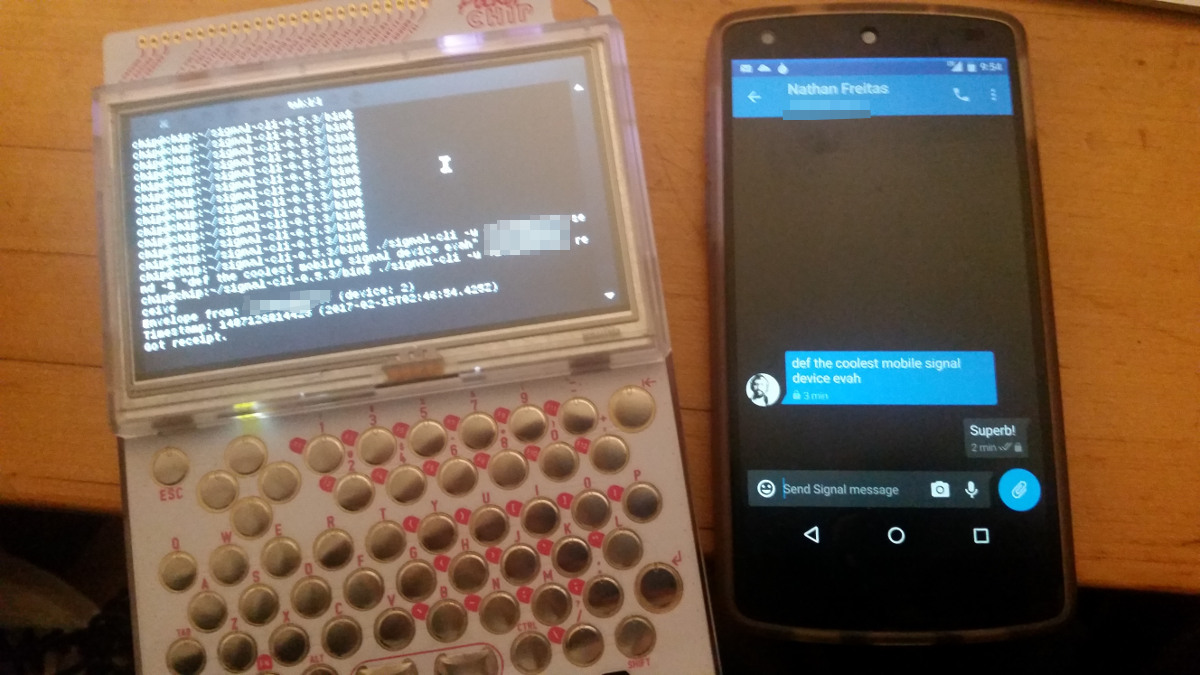
I’m a big fan of the NextThingCo and their $9 CHIP computer for the simultaneously radical and practical approach to hardware manufacturing and low cost computing. Being a fairly early backer of their crowdfunding effort, I was able to get the super fun PocketCHIP dock/case/shell, as well, which looks like a cross between a Blackberry and a Gameboy, with all the circuitous guts exposed. The PocketCHIP is an open-source, handheld, portable computing device, with built-in Wifi and Bluetooth, a hilariously difficult keyboard, and a not so terrible battery. While I have tried to find legitimate uses for it in my day to day toolkit, including as an IoT monitoring terminal for a car’s ODB2 port, I have mostly just carried it to remind myself that the future of mobile computing could be one based on open-source hardware, software and an infinite variety of 3D-printed form factors.
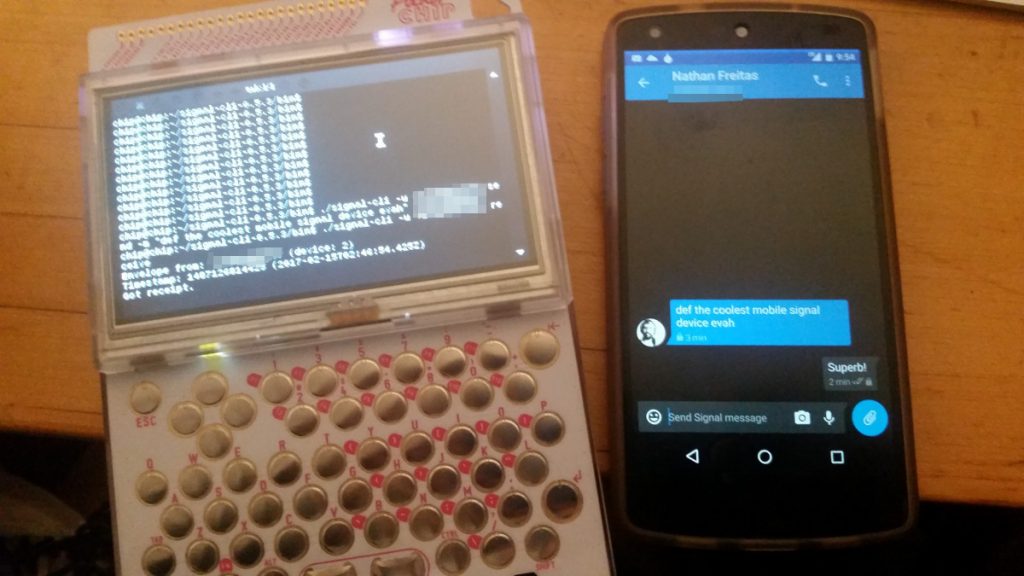
Now, in the last few days, I have become a big fan of Signal-CLI, a Java-based command line interface to the Signal Messenger service. On this very blog, I wrote post on how you can easily send batched encrypted broadcast messages from a terminal shell using it. Then, tonight, I was looking at my PocketCHIP, and I had a moment of inspiration, when I realized that I could easily “apt-get install” java onto it, and by extension run Signal-CLI. This means that I could turn my underused PocketCHIP into a portable, open device upon which to send and receive encrypted messages to anyone in the world who also had Signal.
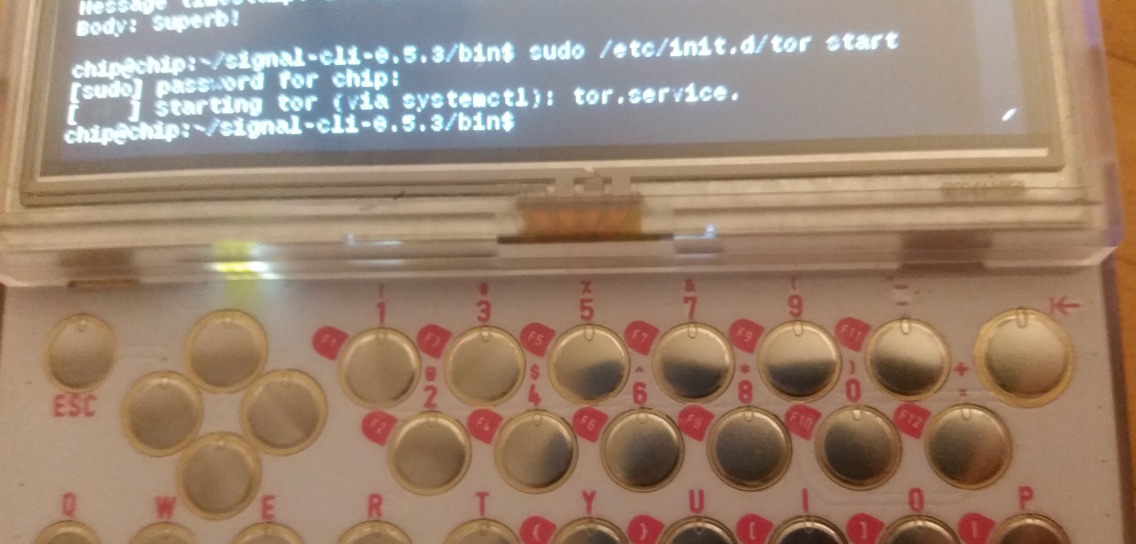
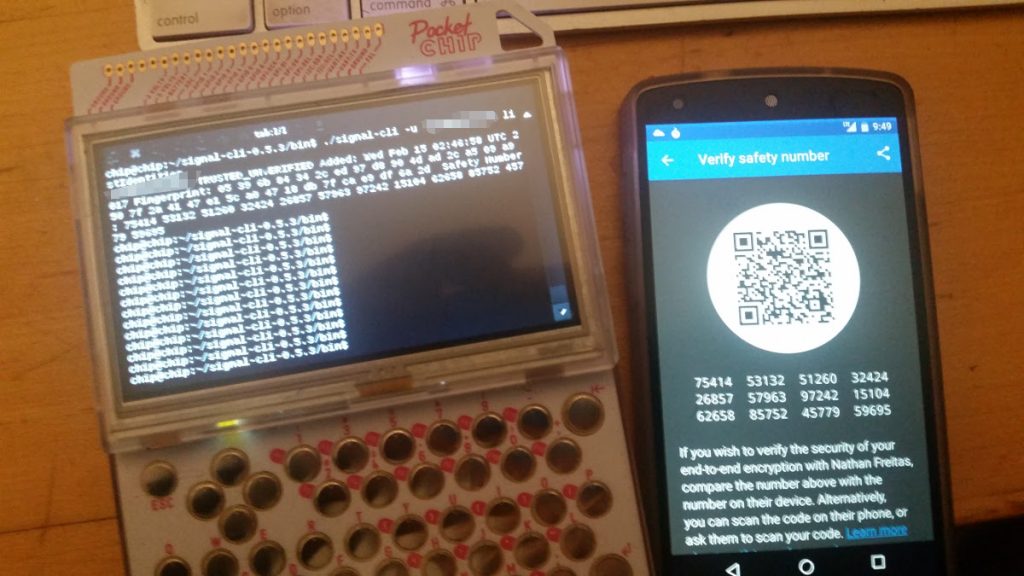
To make a long story short, it works! I installed Java (“apt-get install openjdk-7-jre-headless”), I downloaded the latest Signal-CLI releases (“wget https://tinyurl.com/signalcli035”), unpacked it (“tar xzvf… ” yada yada), and then ran the signal-cli command line. From there, you just follow the simple instructions provided on Github for registering and verifying, and away you go! I used a Google Voice number to handle receiving the SMS verification code. You could also use any landline or payphone – you just need something that can receive a text or voice call. Make sure to follow all the Signal safety tips, as well!
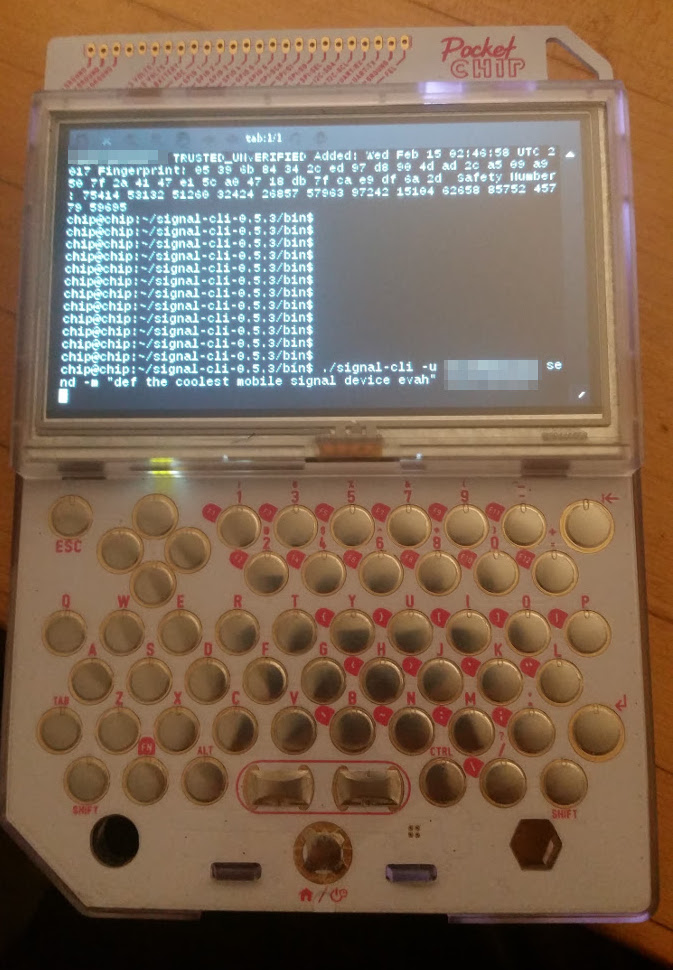
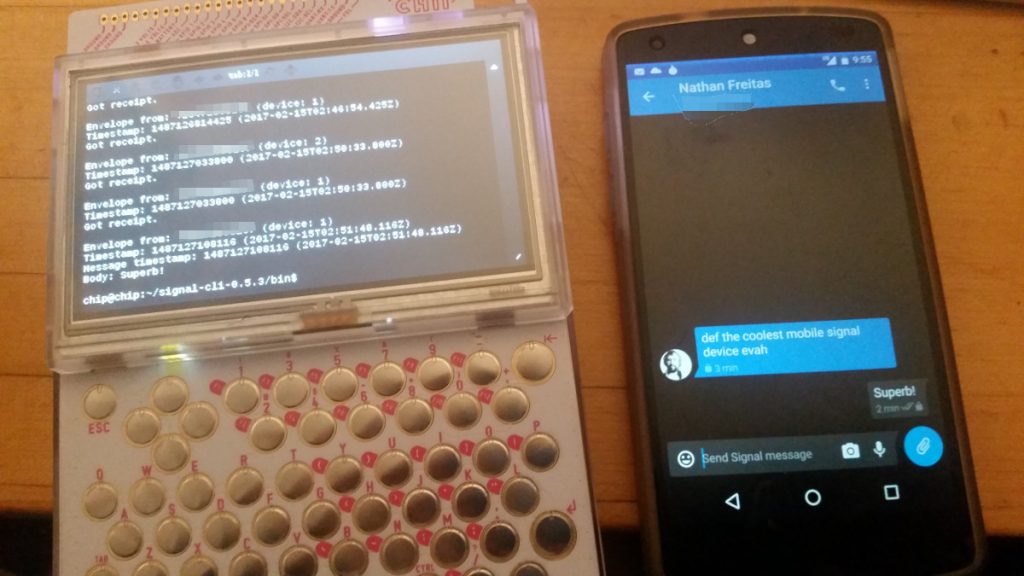
With Signal-CLI, you can send and receive messages, create and manage groups, and even list and verify safety number “keys”. The limited processing power and memory on the PocketCHIP does cause each command to take a few seconds, but that can be worked around. I can easily imaging an ELM or PINE style user interface for this, that would hide all of that fetching and receiving in a background process.
So, now my PocketCHIP is on Signal, and it has become infinitely more useful. Oh, and did I mention, it also runs Tor? Who is up for writing Ricochet-CLI?